Cyber Security in Iowa Counties
Maintained by Iowa Counties Information Technology's Information Security Committee, the Cyber Security in Iowa Counties blog is designed to inform and heighten awareness of cyber security related issues as they apply to Iowa's 99 counties. Our target audience is elected and appointed officials, employees, contractors, service providers and citizens of Iowa counties.
Saturday, March 29, 2014
2014 NACo National Cyber Symposium
For those who may have not heard about it already, NACo is holding an important cyber security event on April 9-11, the 2014 National Cyber Symposium, in Omaha, NE. For more information, check out http://www.naco.org/education/Education/Pages/2014-Cyber-Symposium.aspx. If you are a county official or county IT professional, you won't want to miss this event.
Friday, March 28, 2014
Who has access to your network?
The research into the well publicized breach at Target during the 2013 Christmas shopping season is probably not completely over yet, but a few facts have been well established that I believe provide a great opportunity for counties to learn from someone else's mistakes. For those who may not have been following the story, what has been established is that a successful phishing attack on one of Target's HVAC and refrigeration providers was the initial source of the breach. If you are interested in some of the details, Brian Krebs security blog has probably the best coverage of the story in my opinion. Check out his blog at http://krebsonsecurity.com/2014/02/target-hackers-broke-in-via-hvac-company/.
Just this one fact in the story provides some powerful reminders that county leaders should take to heart. First, phishing has proven once again to be an effective tool in gaining privileged information and in this case access to Target's entire network. Phishing cannot be combated by technology. It's effectiveness can only be reduced through effective awareness training and diligence on the part of our employees and those of our business partners, such as outside contractors and service providers. The second reminder is just how connected everything is today. The access gained through the HVAC contractor ultimately enabled the bad guys to gain access to the point of sale machines throughout Target's organization.
That really brings up the question raised in the title of this post? Who has access to your network? I know in my county's case that our building automation provider has remote access to one of the servers on our network. We were given push back from the vendor because we required them to use two factor authentication in order to gain access. Their argument was that they have multiple employees that need access from time to time and requiring them to use a hardware token every time they needed access was a huge inconvenience. You have to wonder however, if Target had required some form of two-factor authentication if the breach could have been prevented. In such a case, the stolen credentials would have been insufficient for gaining access to Target's network.
It would be wise for county officials to review who has remote access and how much security is in place to prevent unauthorized access. Is remote access truly necessary? We have a number of software providers who demand full time remote access, such as a direct VPN connection so they can access servers to provide support for their products. The problem with such connections is that a breach at the service providers network also means the counties network has been breached. For this reason, we do not allow full time always on connections to our network for any outside service provider. We allow them to connect when needed and we make sure they only stay connected as long as necessary. We get a lot of complaints from some vendors for this approach and sometimes even push back from local officials who are more inclined to trust their outside contractor than their own IT department. But just as in the Target case, compromised access to one system, such as our building automation system, could lead to compromise in other areas of the network. We can't ever forget how connected everything is.
If access for a particular outside service provider is required, what can you do to protect your network? I strongly recommend some form of two-factor authentication, where not only do they need to know something to connect, such as a username and password combination, but they also have to have something in order to complete the process. In our case we require a token generator such as a Yubikey, but there are lots of other options. The reason two-factor authentication is effective is because while a username or password can easily be compromised in a phishing attack, getting possession of a physical object is a lot harder.
The second, and perhaps the most important thing you can do is separate privileges as much as possible. Don't reuse passwords. Don't give administrative access to outside contractors. Give them the minimum amount of permission that they need to provide their service. Isolate services that have outside connectivity as much as possible. This isn't always easy, but keeping tabs on who has access to your network and what access they have is vital to protect your systems from determined attackers.
Just this one fact in the story provides some powerful reminders that county leaders should take to heart. First, phishing has proven once again to be an effective tool in gaining privileged information and in this case access to Target's entire network. Phishing cannot be combated by technology. It's effectiveness can only be reduced through effective awareness training and diligence on the part of our employees and those of our business partners, such as outside contractors and service providers. The second reminder is just how connected everything is today. The access gained through the HVAC contractor ultimately enabled the bad guys to gain access to the point of sale machines throughout Target's organization.
That really brings up the question raised in the title of this post? Who has access to your network? I know in my county's case that our building automation provider has remote access to one of the servers on our network. We were given push back from the vendor because we required them to use two factor authentication in order to gain access. Their argument was that they have multiple employees that need access from time to time and requiring them to use a hardware token every time they needed access was a huge inconvenience. You have to wonder however, if Target had required some form of two-factor authentication if the breach could have been prevented. In such a case, the stolen credentials would have been insufficient for gaining access to Target's network.
It would be wise for county officials to review who has remote access and how much security is in place to prevent unauthorized access. Is remote access truly necessary? We have a number of software providers who demand full time remote access, such as a direct VPN connection so they can access servers to provide support for their products. The problem with such connections is that a breach at the service providers network also means the counties network has been breached. For this reason, we do not allow full time always on connections to our network for any outside service provider. We allow them to connect when needed and we make sure they only stay connected as long as necessary. We get a lot of complaints from some vendors for this approach and sometimes even push back from local officials who are more inclined to trust their outside contractor than their own IT department. But just as in the Target case, compromised access to one system, such as our building automation system, could lead to compromise in other areas of the network. We can't ever forget how connected everything is.
If access for a particular outside service provider is required, what can you do to protect your network? I strongly recommend some form of two-factor authentication, where not only do they need to know something to connect, such as a username and password combination, but they also have to have something in order to complete the process. In our case we require a token generator such as a Yubikey, but there are lots of other options. The reason two-factor authentication is effective is because while a username or password can easily be compromised in a phishing attack, getting possession of a physical object is a lot harder.
The second, and perhaps the most important thing you can do is separate privileges as much as possible. Don't reuse passwords. Don't give administrative access to outside contractors. Give them the minimum amount of permission that they need to provide their service. Isolate services that have outside connectivity as much as possible. This isn't always easy, but keeping tabs on who has access to your network and what access they have is vital to protect your systems from determined attackers.
Monday, December 23, 2013
A Time for Extra Caution
While many associate the holiday season with warm feelings and focus on doing good towards others at this time of year, it is unfortunately a time when the bad guys kick it in to high gear. They know that many people are shopping and looking for bargains, and trying to get all their charitable giving in before the end of the year. It is a perfect time for them to take advantage of us when most of us have our guard down. A tool that is being used more and more by those who want to take advantage of others "good will" at this time of year is cyber attacks.
We have already discussed phishing attacks on this blog in the past, and being cautious in regards to e-mail is warranted all the time, but especially this time of year. A common tactic used in phishing e-mails, and one that has proven to be especially effective is shipping or purchase notification e-mails, chock full of links presumably to track your package or check your order status. Many people order items on-line this time of year, and you may get many perfectly legitimate shipping notification e-mails. The fact that you are expecting a shipping notification e-mail makes this type of attack more effective. You are more likely to click on the links in the message or downloading the attachments without reading the entire message carefully. Don't fall for this trick! Make sure you read the entire e-mail and know how to tell a legitimate shipping notice from a bogus one. The easy and obvious one, did you order the product mentioned in the first place? Hover over links and read the URL that they point to. Does is match the business that sent the notification? On a smart phone, long press on a link to see the actual URL. (Be extra careful here because it can be very easy to accidentally activate the link.) See our article from October 15, 2013 for tips on how to spot a phishing e-mail.
Another thing that can be dangerous this time of year are e-mail and on-line greeting cards. Be very careful with these as well. Do you absolutely know and trust the sender? Perhaps even more importantly, are you confident enough in their tech savvy to be sure they were not duped when they chose a greeting to send? If the answer to either question is no, it is probably best to delete these greetings unopened. Many have dangerous payloads that aren't worth the risk.
It is kind of sad, but unfortunately necessary, that we have to send you these reminders at this time of year. But letting your guard down now can ruin what for many is an enjoyable season.
We have already discussed phishing attacks on this blog in the past, and being cautious in regards to e-mail is warranted all the time, but especially this time of year. A common tactic used in phishing e-mails, and one that has proven to be especially effective is shipping or purchase notification e-mails, chock full of links presumably to track your package or check your order status. Many people order items on-line this time of year, and you may get many perfectly legitimate shipping notification e-mails. The fact that you are expecting a shipping notification e-mail makes this type of attack more effective. You are more likely to click on the links in the message or downloading the attachments without reading the entire message carefully. Don't fall for this trick! Make sure you read the entire e-mail and know how to tell a legitimate shipping notice from a bogus one. The easy and obvious one, did you order the product mentioned in the first place? Hover over links and read the URL that they point to. Does is match the business that sent the notification? On a smart phone, long press on a link to see the actual URL. (Be extra careful here because it can be very easy to accidentally activate the link.) See our article from October 15, 2013 for tips on how to spot a phishing e-mail.
Another thing that can be dangerous this time of year are e-mail and on-line greeting cards. Be very careful with these as well. Do you absolutely know and trust the sender? Perhaps even more importantly, are you confident enough in their tech savvy to be sure they were not duped when they chose a greeting to send? If the answer to either question is no, it is probably best to delete these greetings unopened. Many have dangerous payloads that aren't worth the risk.
It is kind of sad, but unfortunately necessary, that we have to send you these reminders at this time of year. But letting your guard down now can ruin what for many is an enjoyable season.
Monday, October 28, 2013
Mobile Device Security
Hello
Everyone,
This
week we are going to continue our coverage of “Securing the Human” by
discussing Mobile Device Security.
In today’s
busy lifestyles, each of us seem to be more and more glued to our mobile
devices. With that in mind, we also increase the risk of losing those
devices or having them stolen. If your device is lost or stolen, are you
prepared to protect the contents of your device and to ensure that the data
that resides on them is not compromised?
One of
the most effective ways you can protect your information is to secure your
device while you still have it. A great place to start is by enabling
some type of Access Protection, such as setting a PIN, Password or Pattern Lock
that is required to unlock your device before anything can be accessed. This
helps ensure that only authorized users can use and access the information on
your device.

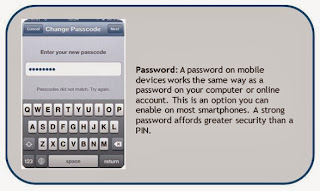

To
establish these settings:
- On an Android Device, it can be setup by going to SETTINGS > LOCATION & SECURITY > SCREEN LOCK
- On an iPhone or iPad, access protection can be setup by going to: SETTINGS > GENERAL > SET SCREEN LOCK
- Once you have set your PIN, Password or Pattern Lock, you will also want to make sure to change the Auto-Lock settings from “None” to a specific amount of time so that the screen automatically locks after a specified time


Another
security feature you can enable is Remote Data Wipe. This allows you to
wipe the device remotely if it is lost or stolen. This can be done on the
device itself to wipe the device after 10 failed passcode attempts, or you can
utilize apps, such as the iPhone / iPad app “Find My Phone” or Android
apps such as “SeekDroid”, “AdroidLost” and “Cerberus”, which will allow you to
access the device remotely from a PC to wipe the device and also allow you to
possibly locate your device if it is still powered on. Check with your IT Department as well, as they may already have processes such as these
in place through corporate policy.
***REMINDER:
More tips on Securing the Human will be given by this year’s fall school
keynote speaker, Lance
Spitzner. You won’t want to miss his eye-opening and thought provoking
presentation.
Also,
don’t miss ICIT being featured in an international webcast given by SANS on
Tuesday, October 29th at 4:00 pm EDT. The story of Iowa Counties Paying IT
Forward will be presented. Click here
for more information and to register.
Until
next week, be prepared and protect your mobile devices!
Thank
you!
Gina
Erickson
IT
Director - Des Moines County
513
N. Main Street
Burlington,
IA 52601
Ph:
319.753.8238
Cell:
319.759.7824
E-Mail:
ericksong@dmcounty.com
Tuesday, October 15, 2013
Clicking Away!
Hi Everyone,
I wanted to continue our discussion about ”Securing the Human.” Many times I will
be removing some spyware or virus from a user’s computer, and I always get
the question, “How did that get in there? Don’t we have stuff that takes care of
this?”
That is a great question! Counties spend thousands of dollars on
security hardware and software to keep our systems from being infected. They do
a pretty good job, but no system is perfect and we need to look at shoring up all
the parts of the county systems. One part of the system that we can strengthen
up right away is the human part. (That means you!)
We, the county employee, need to be educated and made aware of how
we can do our part to make sure our data and computer systems are safe. Many
times a virus or piece of spyware can be traced back to a simple click of a
mouse when we aren't really paying attention. What did that screen say that you
just clicked yes on? One example is the ask.com toolbar. I have had people ask
me how in the world did that get there? What happened too my Google? I then take them
through a java update and low and behold there is the screen during the update
asking if you want to install the ask.com toolbar. Usually most people never
see that screen because they click right through it to get the update; never
understanding they just installed an annoying toolbar on their web browser.
Pretty hard to stop that evil virus or spyware if we are the ones letting it in
past all of the systems.
The Stop.Think.Connect website (http://stopthinkconnect.org/) offers a host of good
information on making us all better users of the internet at work and at home.
You can take all of the cyber education you learn at work and apply that to your
home internet use. Everybody wins!
***REMINDER: More tips on securing the human will be given by this
year’s Iowa State Association of Counties Fall School of Instruction keynote speaker, Lance Spitzner. You won’t want to miss his eye-opening and
thought inducing presentation.
Also, don’t miss ICIT being featured in an international webcast
given by SANS on Tuesday, October 29 at 4:00 pm EDT. The story of Iowa Counties "Paying IT Forward" will be presented. Click
here for more information and to register.
Next week I want to focus on Phishing. It is probably the nastiest
and most effective tool that hackers are using to get into county systems, and we need to
spend a little time and focus on educating ourselves on how to dodge this very
nasty bullet.
Thank you,
Joel Rohne
IT/GIS Worth County
641.324.3668
Phishing and Spear Phishing
No doubt you have heard the term "phishing", but perhaps you are not quite clear on what it is. More recently it seems we hear more about "spear phishing". What is the difference? How can you protect yourself?
Wikipedia has a great article on phishing that explains both terms, some of the history of the practice, including how it got its name, and many of the specific techniques used. Like many security related resources however, some of it can get fairly technical, making it difficult for some to understand what it means to them. The story of how the name "phishing" came about is fairly geeky and technical and relates to when the practice first became prevalent on America On Line. Regardless of how the name actually came about, I think it is a good metaphor for describing the practice. When I think of literal fishing, two methods come to mind, the kind of fishing I used to do with my dad, where we would drop a line in the water and hope something came along and took a bite, or the TV documentaries showing commercial fishermen casting these huge nets to pull in a large haul. Both of these images could be used to help explain the practice of phishing. The goal is to catch someone off guard and steal information from them, such as usernames, passwords, financial account information, real money, etc.
The dropping a line and waiting for someone to bite image aptly describes phishing because e-mail (or in some cases a phone call) are used to deliver the bait, and the bad guys are just hoping that someone takes it. A message might indicate that your account is about to expire. Or maybe you need to renew some information to keep receiving some benefits or services. Or perhaps there is something "you just have to see!" When you click the link suggested, instead of taking you to a legitimate web site, it takes you to a site where you enter the sought after information and the bad guys now have it. In many cases, both the e-mail and the web site might look very convincing. In other cases, opening a malicious attachment is the action desired, infecting your computer with mal-ware, which can then be used to gather more information from you or to enable your computer to be used to attack others.
The casting a wide net image also aptly describes phishing because that is generally how the bad guys operate, sending their e-mails to a wide audience, perhaps thousands or even millions of targets. The wider they cast the net, the more likely they are to get numerous victims to take the bait. The problem for the bad guys when it comes to phishing is that the larger the net cast, the harder it is to make the message look appealing. For example, if I receive an e-mail that my account at a bank needs renewed, but I don't bank there, I am not likely to take the bait. Many people who get the message will be a customer of that bank, but not everyone, and the more bogus e-mails someone receives, the more aware they become that they might eventually be a target of a phishing attack. Over time, as awareness increases, phishing can become less effective for some targets. It is still effective, so it keeps happening and there is still a need to alert, but the bad guys have, as they always do, changed their tactics to become more effective.
Spear phishing has become more prevalent in recent years. The difference between spear phishing and regular phishing, is that the spear phishing attacks are much more targeted. In literal spear fishing, you have to get up close and personal with your target, taking careful aim and striking at just the right time. Spear phishing is like that. The bad guys take the time to get to know their targets, the specific products or services they use, the timing of important events in their life, really as much as they can about them. The target of the attack is also much smaller, a small specific group of persons, or perhaps in some cases even directed at a specific individual, so the messages can be very personal and perhaps very relevant to what may be important to them at the time. The more targeted the bait, the more difficult to spot and the more likely someone will bite. A recent spear phishing attack targeted at executive level state employees has been in the news. A sample subject is "Annual Form - Authorization to Use Privately Owned Vehicle on State Business". Perhaps you can see how someone might be inclined to open the attached form. If their authorization isn't up to date, they may not get reimbursed for their expenses. In this particular attack, the CryptoLocker ransom-ware is the mal-ware embedded in the attached form, which was mentioned in a previous blog post.
So how can you protect yourself from phishing and spear phishing attacks? Learn how to spot the bait. If an e-mail looks suspicious in any way, it is safest to err on the side of caution. Be especially suspicious of e-mails that create a sense of urgency or require immediate action. E-mails with a generic salutation, such as "Dear Customer", are also a red flag. Also watch out for e-mails with a lot of grammar or spelling mistakes. Legitimate businesses will usually proofread their communications carefully prior to sending them. Don't trust links or attachments. From your PC, you can hover your mouse over a link to see the actual target address. If it doesn't match what it displayed, this should raise an alarm. On a mobile device, previewing the link can usually be accomplished by pressing and holding the link, causing a popup to be displayed. Be careful though, it can be easy to accidentally click the link. As for attachments, only open ones that you were expecting is a good, safe practice. Also, don't be quick to trust the sender. Just because an e-mail indicates it is from a trusted friend, it doesn't mean that they actually sent it. The sender address can be forged, their computer may be infected with mal-ware, or their e-mail account could have been compromised (probably because they fell victim to a phishing attack). If you receive an e-mail from a friend that contains links or attachments, contact them by another means to verify they actually sent it.
By using common sense and being generally cautious when using e-mail, you can help protect yourself and others from becoming a victim of a phishing attack.
Wikipedia has a great article on phishing that explains both terms, some of the history of the practice, including how it got its name, and many of the specific techniques used. Like many security related resources however, some of it can get fairly technical, making it difficult for some to understand what it means to them. The story of how the name "phishing" came about is fairly geeky and technical and relates to when the practice first became prevalent on America On Line. Regardless of how the name actually came about, I think it is a good metaphor for describing the practice. When I think of literal fishing, two methods come to mind, the kind of fishing I used to do with my dad, where we would drop a line in the water and hope something came along and took a bite, or the TV documentaries showing commercial fishermen casting these huge nets to pull in a large haul. Both of these images could be used to help explain the practice of phishing. The goal is to catch someone off guard and steal information from them, such as usernames, passwords, financial account information, real money, etc.
The dropping a line and waiting for someone to bite image aptly describes phishing because e-mail (or in some cases a phone call) are used to deliver the bait, and the bad guys are just hoping that someone takes it. A message might indicate that your account is about to expire. Or maybe you need to renew some information to keep receiving some benefits or services. Or perhaps there is something "you just have to see!" When you click the link suggested, instead of taking you to a legitimate web site, it takes you to a site where you enter the sought after information and the bad guys now have it. In many cases, both the e-mail and the web site might look very convincing. In other cases, opening a malicious attachment is the action desired, infecting your computer with mal-ware, which can then be used to gather more information from you or to enable your computer to be used to attack others.
The casting a wide net image also aptly describes phishing because that is generally how the bad guys operate, sending their e-mails to a wide audience, perhaps thousands or even millions of targets. The wider they cast the net, the more likely they are to get numerous victims to take the bait. The problem for the bad guys when it comes to phishing is that the larger the net cast, the harder it is to make the message look appealing. For example, if I receive an e-mail that my account at a bank needs renewed, but I don't bank there, I am not likely to take the bait. Many people who get the message will be a customer of that bank, but not everyone, and the more bogus e-mails someone receives, the more aware they become that they might eventually be a target of a phishing attack. Over time, as awareness increases, phishing can become less effective for some targets. It is still effective, so it keeps happening and there is still a need to alert, but the bad guys have, as they always do, changed their tactics to become more effective.
Spear phishing has become more prevalent in recent years. The difference between spear phishing and regular phishing, is that the spear phishing attacks are much more targeted. In literal spear fishing, you have to get up close and personal with your target, taking careful aim and striking at just the right time. Spear phishing is like that. The bad guys take the time to get to know their targets, the specific products or services they use, the timing of important events in their life, really as much as they can about them. The target of the attack is also much smaller, a small specific group of persons, or perhaps in some cases even directed at a specific individual, so the messages can be very personal and perhaps very relevant to what may be important to them at the time. The more targeted the bait, the more difficult to spot and the more likely someone will bite. A recent spear phishing attack targeted at executive level state employees has been in the news. A sample subject is "Annual Form - Authorization to Use Privately Owned Vehicle on State Business". Perhaps you can see how someone might be inclined to open the attached form. If their authorization isn't up to date, they may not get reimbursed for their expenses. In this particular attack, the CryptoLocker ransom-ware is the mal-ware embedded in the attached form, which was mentioned in a previous blog post.
So how can you protect yourself from phishing and spear phishing attacks? Learn how to spot the bait. If an e-mail looks suspicious in any way, it is safest to err on the side of caution. Be especially suspicious of e-mails that create a sense of urgency or require immediate action. E-mails with a generic salutation, such as "Dear Customer", are also a red flag. Also watch out for e-mails with a lot of grammar or spelling mistakes. Legitimate businesses will usually proofread their communications carefully prior to sending them. Don't trust links or attachments. From your PC, you can hover your mouse over a link to see the actual target address. If it doesn't match what it displayed, this should raise an alarm. On a mobile device, previewing the link can usually be accomplished by pressing and holding the link, causing a popup to be displayed. Be careful though, it can be easy to accidentally click the link. As for attachments, only open ones that you were expecting is a good, safe practice. Also, don't be quick to trust the sender. Just because an e-mail indicates it is from a trusted friend, it doesn't mean that they actually sent it. The sender address can be forged, their computer may be infected with mal-ware, or their e-mail account could have been compromised (probably because they fell victim to a phishing attack). If you receive an e-mail from a friend that contains links or attachments, contact them by another means to verify they actually sent it.
By using common sense and being generally cautious when using e-mail, you can help protect yourself and others from becoming a victim of a phishing attack.
Tuesday, October 1, 2013
We Don't Negotiate with Terrorists
The timing was ironic. Last night I was at the office when the date
changed to October 1, 2013; the beginning of National Cyber Security Awareness
month. The reason I was at the office
was due to a user installing the CryptoLocker ransomware on their machine. This particularly nasty and ingenious piece
of software encrypts all of the Word, Excel, PDF, and image files it can find
on local and network drives. It then
taunts you with the ransom, $300, to get all of your documents decrypted.
The user had opened an innocent looking
email with a zip attachment. Inside that
zip attachment was an executable file designed as a major money maker for these
criminals. It was a spear phishing
attack and it worked.
I first found out about the issue at
around 10:30 p.m. when my phone started buzzing the buzz of numerous emails
arriving. I was shocked when that number
showed 160+ unread emails and it was climbing quickly. The emails were from the antivirus agent installed
on that machine sending out alerts that something malicious was being
blocked. So I logged onto that machine
and saw the CryptoLocker window along with a note that all files are
encrypted. The threat had managed to get
through our email filter and our up to date antivirus agent was helpless to
stop it.
I immediately turned off the
machine and drove in to work to fix whatever damage it had caused. I restored the network files that had been
encrypted, but the local files were unrecoverable. We restored the machine from our image and
the user lost a day’s work. Paying the
$300 was never an option, we don’t negotiate with terrorists.
We have done some phishing attack
training with our users but that didn't stop this attack. I sent out an email to all users late last
night telling them to be alert and think before opening email attachments or
clicking on email links. I included a
link to the July, 2013 OUCH! Newsletter from SANS that talked about spear
phishing. I think the message was heard
loud and clear because it hit close to home.
It was also a good reminder that I need to do a better job protecting
our network. When attacks like this
materialize you go through the steps you could take to prevent it from
happening again in the future.
National Cyber Security month gives
you an excellent platform to push for more security and training for your
users. These threats are real and they
can happen to you.
Subscribe to:
Comments (Atom)
